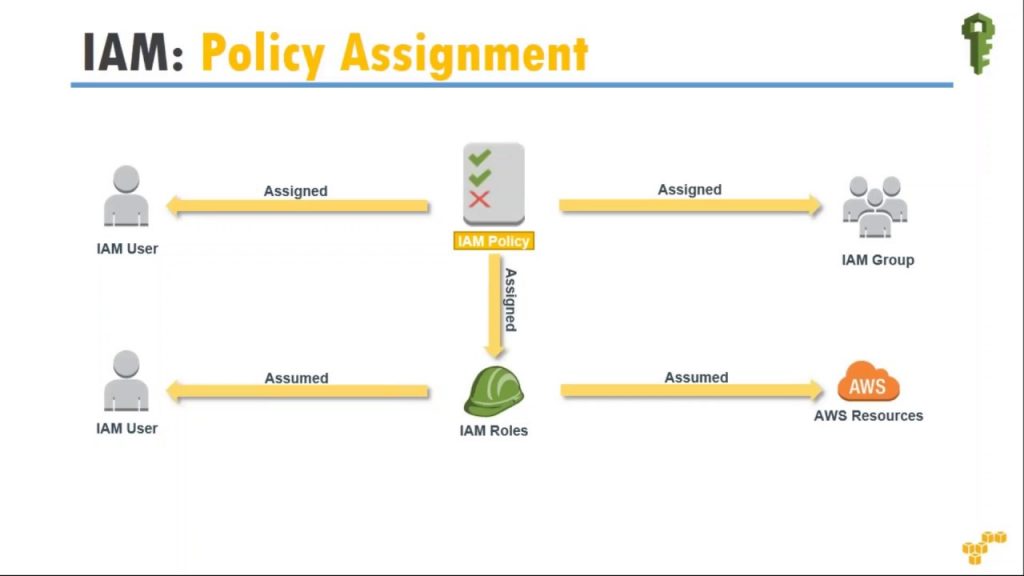
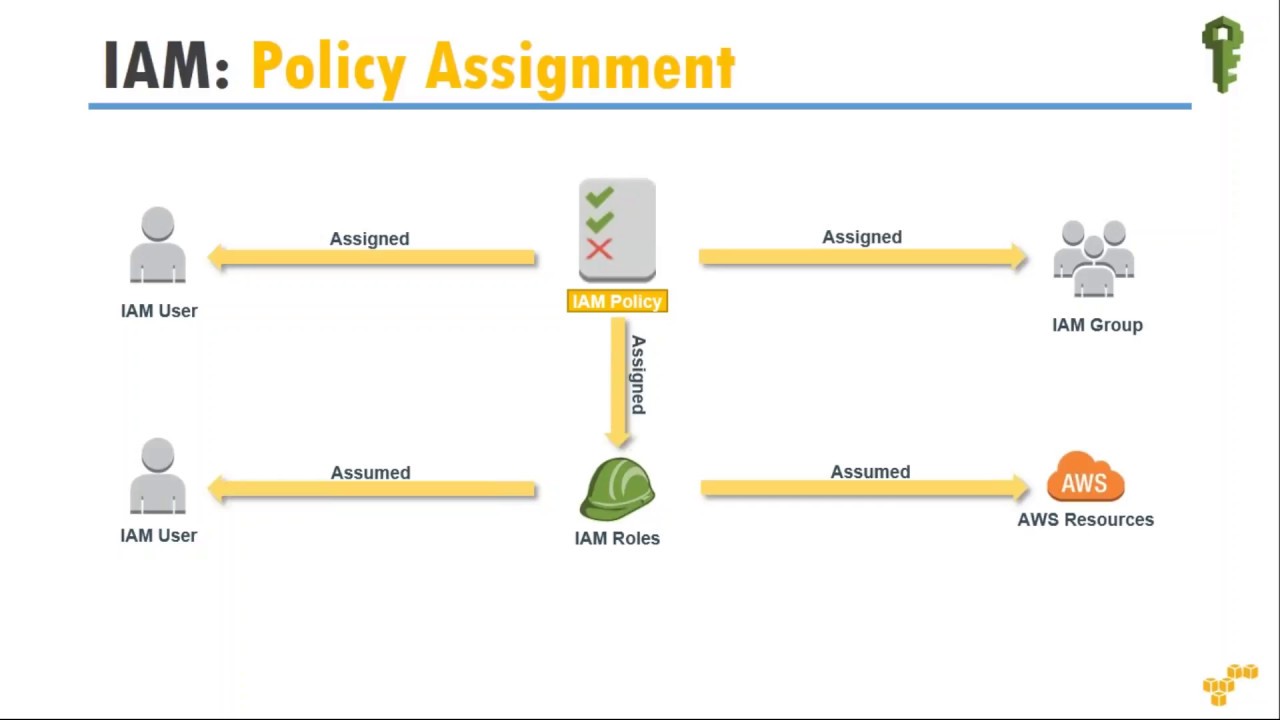
In this IAM essentials, we will look into the important aspects of IAM and its functionalities.
IAM Basics
1. AWS Identity and Access Management (IAM) – Create users and groups to manage your AWS resources. Individual permissions can be applied using policies.
2. Granular policies can be applied to users and groups on AWS resources (eg: start instances, stop instances etc..)
3. IAM also provides federated access. Using which, anyone without aws credentials can use AWS console or API’s. The access can be configured with services like AD, AWS Directory services, Amazon Cognito or any other open Id services like facebook and google.
[alert-announce]RECOMMENDED COURSES
AWS Certified Solutions Architect (2018)
AWS Certified Developer Associate level (2018)
AWS Certified SysOps Administrator Associate (2018)
[/alert-announce]IAM Authentication
1. Supports multifactor authentication.
2. Supports temporary security credentials for accessing AWS services using STS (security token service).
Temporary Credential Scenarios
Identity Federation
You can have the following identity federation schemes.
1. Enterprise identity federation: Uses Security Assertion Markup Language (SAML) 2.0. Can be used with Microsoft AD FS, Shibboleth etc. Basically, any identity provider with SAML 2.0 support can create a single sign-on system using STS. You can also use a custom federation service using URLs ( code based) to connect to AWS using STS tokens.
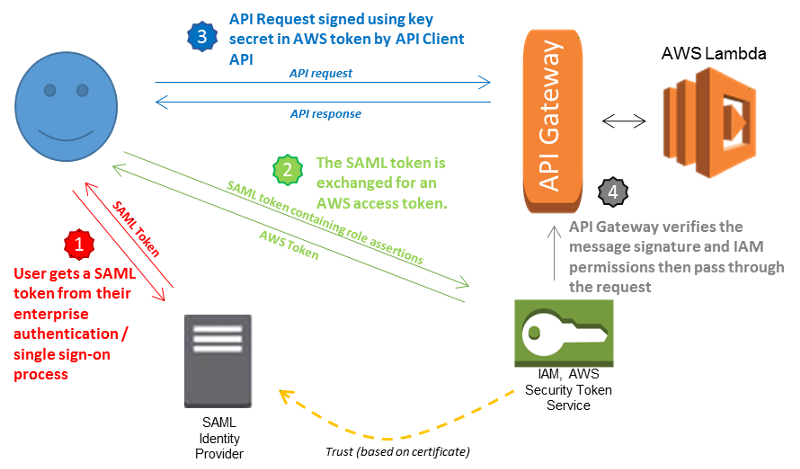
2. Web-based Federation: using openId like facebook, google, amazon cognito etc..
3. Cross-account Access Role: You can create IAM roles with permissions for other AWS linked accounts or third party accounts to access resources on your account.
4. ec2 instance role: Rather than saving the access and secret key on the server for API calls, you can create a role and attach it to the instance. So you can make API calls without a permanent access key and secret key.
IAM user Credentials
An IAM user can have the following type of credentials.
1. Access Keys and password (For CLI, API access). You can set policies for passwords.
2. X.509 (For CLI access)
3. SSH keys (For code commit )
Note: User access keys and X.509 certificates can be rotated.
IAM roles
An IAM roles are designed to make API and CLI calls to AWS services without an Access Key and Secret key. Once you attach a role to an ec2 instance, it will be able to make API calls to allowed services in the policy which is attached to the role. You can attach a role to an IAM user also.
1. You can have a maximum of 250 roles. You can increase the limit using special request form. If you want many roles, you can go for temporary access using STS.
2. You cannot attach a role to a group.
3. You cannot attach a role to a running ec2 instance.
4. You can also attach a role to ASG launch configuration.
5. You can restrict an IAM user to attach only specific roles to instances.
IAM Service Role
A service role is an IAM role which is associated with AWS managed services like EMR, Elastic Bean Stalk, Ops works etc. A service role is required by these managed services to assume a role in making API calls to other AWS services.
IAM Instance Profile
Instance profile is a container to hold an IAM role. This can be attached to an instance. When you create a role using AWS management console, by deafult an instance profile will be created with the same name as the roles name. Whereas when you create a role using CLI, only role will be creates. You need to create an instance profile with the same name as the role or a different name.
Note: Please help us update this doc if you think some more information can be added.