In this post, you will learn how to expose Docker engines API for remote docker command execution through REST APIs
What is Docker remote API?
The primary use of a Docker remote API is to connect with the Docker engine remotely. Let's say you are running the docker host on a remote server and you want to connect to it from your laptop. For this scenario, you can use the remote API and connect to it using the REST API's as the docker engine accepts REST requests.
One more use case is that let's say you have an application and you want to get the details of the containers in docker host. For this, you can use the remote API feature.
Docker Courses You Might Like
- Docker Mastery: The Complete Toolset From a Docker Captain
- Learn DevOps: The Complete Kubernetes Course
Enable Docker Remote API
All the docker configurations are present in the file/lib/systemd/system/docker.service. In that file, there is an ExecStart parameter.
Open the file/lib/systemd/system/docker.service, search for ExecStart and add value as shown below.
ExecStart=/usr/bin/dockerd -H tcp://0.0.0.0:4243 -H unix:///var/run/docker.sock
The above command will bind the docker engine server to the Unix socket as well as TCP port 4243. "0.0.0.0" means docker-engine accepts connections from all IP addresses.
Note: Also, please add necessary firewall rules for your server to accept connection on port 4243
Now for all the changes to take place, you need to restart the daemon and Docker service. Execute the following commands to do that.
sudo systemctl daemon-reload sudo service docker restart
Now, remote API is enabled on your docker host. To test this, there are a few ways.
How do I access Docker API?
You can use curl command-line utility or REST APIs to access the Docker API. Both ways are explained below.
Test using curl
Get the IP address of your Docker host where you enabled remote API and execute the following command from any terminal which supports curl. You can test with the localhost as well.
Note: replace the IP with your Docker host IP or localhost as shown below.
curl http://localhost:4243/version curl http://35.225.233.5:4243/version
The above command will output all the images in your docker host in JSON format.
You Might Like: Docker Useful Hacks
Test using a REST client
You can test the API using REST client like Postman. If you use the following URL in your REST client, you will get the JSON output in a prettified manner as shown in the image below.
http://192.168.5.5:4243/images/json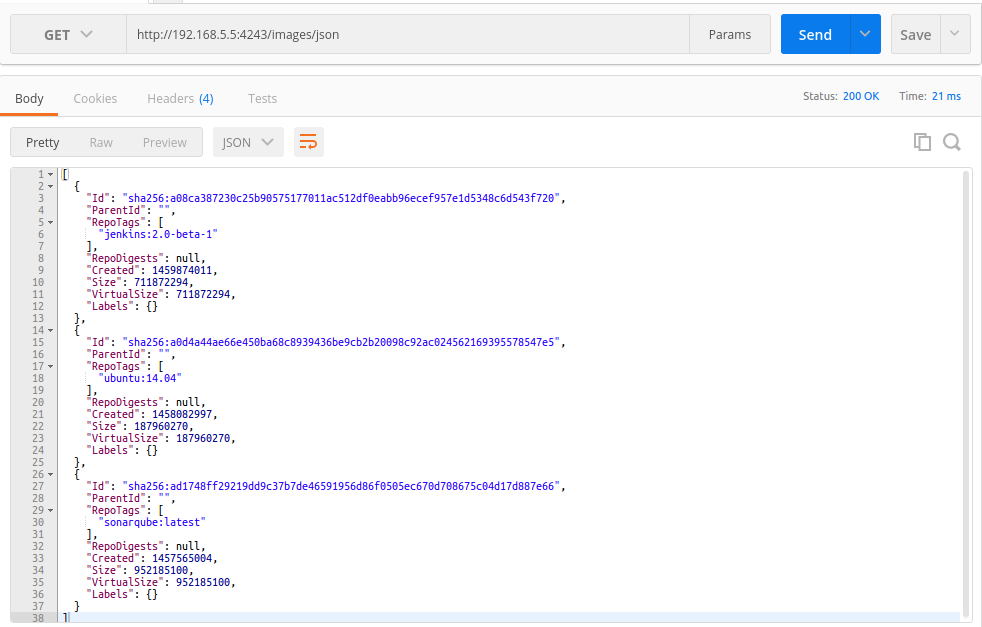
In this tutorial, you learned to enable Docker remote API. For better security, you can use certificates with the REST requests. That we will cover in another detailed post If you face any issues with this setup, let us know in the comments section.